How to Advertise Subnets to Upstream Routers With OPNsense and ARP
Aug 2, 2018 · 3min read
If you ever wondered how to split a subnet away from a fixed upstream gateway, here’s how you can achieve this with ARP in OPNsense.
Today was the first time that I needed to split one IPv4 subnet into two and forward the second half to somewhere else—without the ability to configure the upstream gateway. It took me a while to figure out how to achieve this with an OPNsense firewall as my router. I thought I’d document this in case anyone else is looking for a solution to this, too.

The Challenge of Transparently Splitting a Subnet ¶
Consider the following scenario: My ISP allocated me a /28 subnet (x.x.129.208/28). Along with it, they provided a gateway on the first IP of the subnet (x.x.129.209) and nothing else—and that was the problem.
Usually, when you are provided a subnet, it is routed to the fixed public IP of your router. This IP is not part of the subnet so you have the freedom to forward the routing of the subnet downstream over any number of hops to anywhere you need it in your infrastructure. In this case, however, the first IP was assigned to the ISP gateway—making it impossible to allocate the subnet somewhere else. My router had to be in the same subnet (i.e. x.x.129.210).
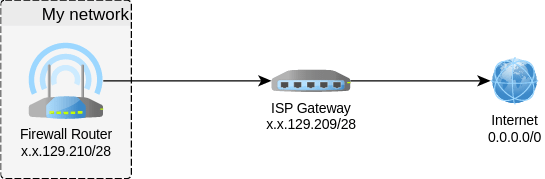
However, what I wanted was a DMZ behind that firewall router, i.e. servers that are accessible via public IPs without NAT or Transparent Bridging. So I split the /28 subnet in two /29:
x.x.129.208/29x.x.129.216/29
This is how it looked once configured on the firewall router and DMZ:
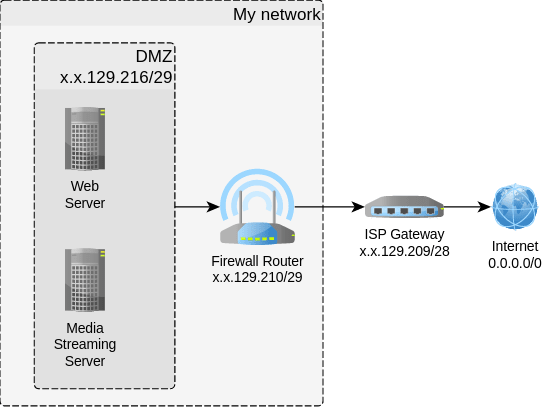
Notice how the firewall router has the same Internet-facing IP but with a different netmask now?
I thought that the OPNsense firewall router would be intelligent enough to advertise to the upstream ISP gateway, that the IP x.x.129.210 and all IPs x.x.129.116-.123 of the /29 DMZ subnet were all to be routed via its ISP-facing IP (x.x.129.210).
But no, it doesn’t work like this out of the box. And there was no way for me to explicitly configure the ISP gateway to route the /29 DMZ subnet to a specific IP.
The Solution: Proxy ARP ¶
After lots of DuckDuckGoing (If searching with Google is called Googling, then that’s what searching with DuckDuckGo must be called, right?) to no avail, I finally stumbled over the Virtual IP settings in OPNsense, specifically of type Proxy ARP.
This Proxy ARP type of virtual IP allows you to broadcast the advertisement of IPs or subnets via an interface. So I entered:
- Mode: Proxy ARP
- Interface: WAN
- Address:
x.x.129.216/29
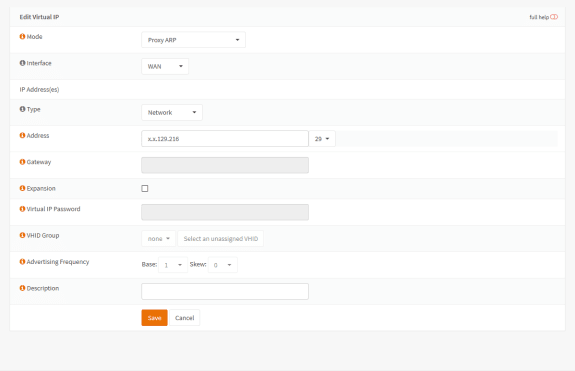
In other words: The OPNsense firewall router now published to the ISP gateway that (besides the IP x.x.129.210) it also was the recipient for all IP packets of the /29 DMZ subnet. In a way, ARP allows configuring upstream routers that are not part of your infrastructure.
This works like a charm. Servers in the DMZ configured with the public IPs of the second /29 subnet are now able to communicate in both directions with the Internet.
Reminder ¶
OPNsense automatically adds the DMZ subnet to its NAT, so don’t forget to remove it manually. In this case, it was translating the public subnet x.x.129.216/29 to the public IP x.x.129.210—which of course doesn’t make any sense whatsoever. It might work in the outbound direction, but your DMZ can’t be reached from the outside, rendering the DMZ useless.

Michael Schmidle
Founder of PrioMind. Start-up consultant, hobby music producer and blogger. Opinionated about strategy, leadership, and media. In love with Mexico. This blog reflects my personal views.
Jul 11, 2024 · 3min read
Integrating Termly With Nuxt 3
Integrating Termly’s consent management with Nuxt 3 turns out to be harder than just inserting a script tag. Here’s a solution that resolves hydration mismatches and UI glitches, ensuring smooth functionality and user experience. Continue…
Nov 15, 2023 · 2min read
Mastering Keyboard Interactions in Shadcn-Vue: A Fix for Complex UIs
In the intricate dance of UI components within Vue applications, a misstep can disrupt the rhythm. Discover how a straightforward tweak can harmonize your keyboard interactions in shadcn-vue in complex nested components. Continue…
Sep 26, 2023 · Nov 11, 2023 · 2min read
The Better Nuxt Directus Authentication Middleware
The Nuxt Directus docs give you a basic auth middleware, but it’s got some quirks. Here’s how to bulletproof it. Continue…
Apr 18, 2020 · 6min read
Accelerate Your Website—With Your Logo
Most people who care about their website’s performance probably use a website logo created by vector graphics software. Here’s how to take advantage of vectorized logos to speed up your website. Seriously. Continue…



